XSS Vulnerability
Found in ConnectWise Remote Access Platform With Great Potential For Misuse by Scammers

Nati Tal
November 23, 2022
•
8
min read
Following our analysis of Remote Access Tool (RAT) abuse, we turned to analyze the misuse of one of the most powerful platforms in that market — ConnectWise. During the analysis a vulnerability in the hosted platform was found, one that can be exploited by scammers to take control of this powerful tool with no limitations — and not a penny spent. In this write-up we will share the technical details of this Stored XSS vulnerability, exploiting it, and also how ConnectWise quickly responded to this disclosure and helped make their platform much safer for the benefit of us all.

Providing remote assistance or managing a remote fleet of computers became quite mandatory for every IT department, from huge corporates to even small teams with one IT guy that does all the magic. One of the most advanced services for remote control and support is provided by ConnectWise in the form of a fully hosted cloud service with tons of customizations and compelling features. We’ve learned about ConnectWise during our endeavors in the RAT Scams world, as this platform is also heavily abused by scammers remotely hijacking victims’ computers to grab all their accounts, credentials, files, and whatnot.
For bad actors, it is quite simple to create an account, for free, and start a 14-day fully-featured trial just ready to be abused. Putting on the scammer’s hat, we mimic the way a scam starts by creating a fake support portal that will be used to install RAT agents on victims’ computers. We realize that all you need is a free anonymous email account and some fake personal details, and in a matter of seconds we get our hands on an operational support portal with a corporate-grade RAT (Remote Access Tool) agent, and you can even use the powerful customization feature to change the look to mimic a real product/company support page — without even one line of code written:

For a scammer, all left is to call the victims and manipulate them as if they have some computer technical issue, or alternatively as in our example — send them a fake invoice for some service they never registered to, urgently referring them to a page like this fake refund service portal to enter the “invoice” code (triggering the dedicated silent RAT installation).
Note that ConnectWise is well aware of those scams, and has lately added this noticeable advisory on the main page — visible on all trial/free accounts:

This is a great move by ConnectWise and a good start! Yet this is not enough and can even be removed as we will see later on…
Now is where those powerful customization options can also introduce some bad attack vectors. An XSS (Cross-Site Scripting) Vulnerability is a case in which the attacker manages to exploit a security bug in a system to alter the code executed on another website. Altering the code allows control on the webapp from the real (and trusted) context — as if the code was executed by the trusted author of service. This is quite powerful and has tons of harmful exploitation vectors.
Going back to our case here, as mentioned above, the webapp admin has control over text and images stored on the servers and served as part of the portal webapp to any visitor. For most of the customizable textual elements, there is decent validation and sanitation. Meaning, trying to insert HTML/JS tags and content to those components instead of just text and titles will not lead to injecting those into the webapp. The unwanted text bits are mostly just deleted automatically (e.g.
This kind of customization is easily done on the administration page of the ConnectWise Control portal, in which you can choose the Appearance tab and have control over hundreds of resources:

After testing and validating several attack vectors, we have found that in the case of the Page.Title resource, the above is not being taken care of, leaving it vulnerable to a “Stored XSS” exploitation. The user’s input is inserted directly, as is, in between the
Here we can see the Page.Title resource that controls the content of the HTML page title. Specifically, what goes in between the
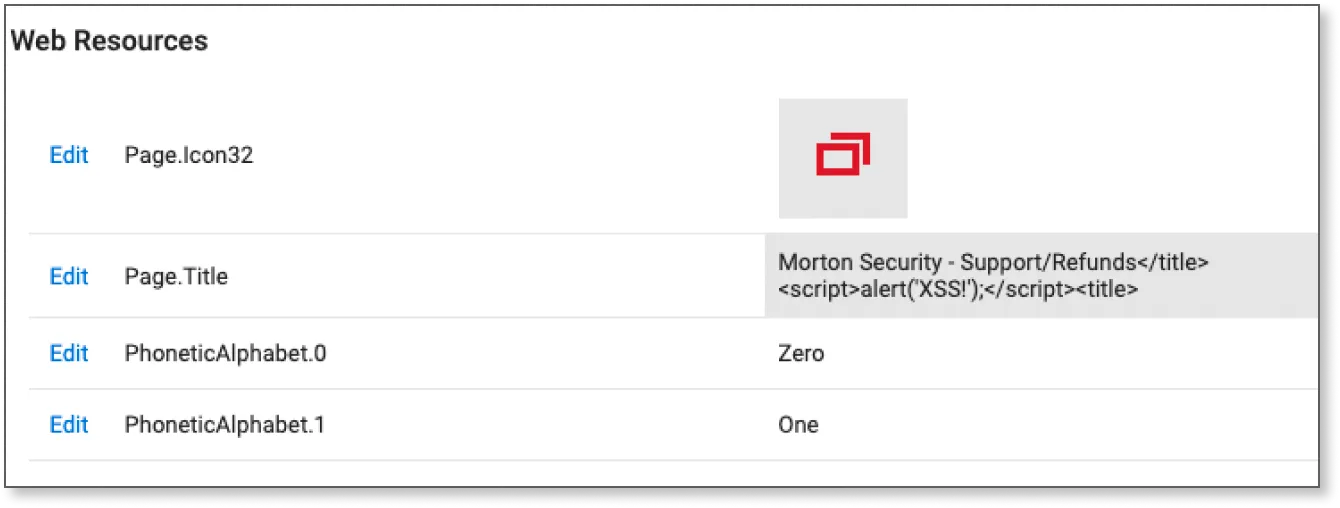
As you can see above, the title was altered from a generic “Support Portal” text-only string to a combination of HTML tags and JavaScript code. If we take this new string and place it in between the title tags we will get this (where the new injected text is bold):
We’ve successfully injected a simple script into the page, right next to its’ title. It was important to close and re-open again the

Success! But this is just the beginning… as being able to inject code into the page is much more powerful than just this simple alert popup. A script executing from this context gives an attacker full control over any element of the webapp, potentially altering any element of the page as well as connection to the backend servers. This can harm any potential visitor (running malicious js code, altering downloaded RAT agents, etc).
Moreover, this can be used to abuse the hosting services itself — allowing misuse of ConnectWise hosting, identity, and certificate to serve malicious code or gain full access to admin pages even after the trial period is over.
let’s put the scammer's hat on for a second. Remember that Advisory box? The one ConnectWise added to draw the attention of visitors to the possibility this trial account is being abused for scamming. Well, as a scammer, I don’t want this box there of course. So why not just remove it?
With this vulnerability, the scammer can control all parts of the webapp page. The advisory box is no different. Looking for it on the page code we see it is being added dynamically after testing for the account type, and presented in a graphical box under the class name InfoPanel. So the piece of code we would like to execute should just look it up and set it to be hidden — like this:
document.getElementsByClassName('InfoPanel')[0].style.visibility='hidden';
Well, there is also a simple catch here we still need to overcome — this infobox is being added dynamically. So to avoid a race condition here (and do a getElementsByClassName when the element is not yet available) we will add a listener to wait for the page to finish loading. Oh, and also some console printouts just for fun:
console.log('Yep, we are running code here...');
window.addEventListener('load', function() {
console.log("Removing the advisory message");
document.getElementsByClassName('InfoPanel')[0].style.visibility = 'hidden';
});And now putting this all together into the Page.Title element, adding the
Morton Security - Support/Refunds</title>
<script>console.log('Yep, we are running code here...');
window.addEventListener('load', function () {
console.log("Removing the advisory message");
document.getElementsByClassName('InfoPanel')[0].style.visibility='hidden';
});
</script>
<title>And that’s it! Quick refresh to the portal page and now we have the same portal, free of charge and without the advisory. Look at the debug console on the right to see the console printouts and also the updated

It was super important for us here at Guardio to disclose this simple yet powerful vulnerability to ConnectWise as soon as possible. We’ve seen too many abuses of their platform and too many victims losing their life savings to those relentless scammers. Adding this vulnerability to the scammers' toolbox is a big no-no.
ConnectWise was very responsive and quickly fixed the issue and deployed the new release to all users on the 8th of August 2022 on version v22.6 and above. As requested by ConnectWise, we waited at least 30 more days before this disclosure so on-prem users will get the chance to update their installations as well.

Indeed, now the Page.Title element is sanitated correctly, leaving our exploit code filled with escaped characters and quite unreadable but most importantly — un-executable:
<title>Morton Security - Support/Refunds</title><script>
console.log('Yep, we are running code here...');
window.addEventListener('load', function () {
console.log("Removing the advisory message");
document.getElementsByClassName('InfoPanel')[0].style.visibility='hidden';
});</script><title>
</title>We must also mention another action ConnectWise took which is completely disabling the customization feature for trial accounts. This is a bold move! No more fake Amazon/Microsoft and other major brands' support pages on the hosted service! And on the other hand, business-wise, ConnectWise won’t allow legit customers to try out one of their most differentiating features in this market! They sure took this matter seriously which is very appreciated and will surely help make web browsing safer and the scammers' life a bit harder.
Vulnerabilities and other security issues, like the above, will keep on popping up and being exploited by bad actors in almost any possible way. As part of the security community, here at Guardio Labs, we are obligated to explore, find and disclose any security issue we find — just so it will be remediated before those bad actors will even get a chance to exploit it.
ConnectWise was super responsive and is very much security aware, so it was a pleasure to work with them on fixing this vulnerability and also adding the final touch of removing the customization feature.
Want to learn more about those nasty scams? Read our full analysis:
Oh RATs! — How Guardio found a way to detect the nastiest of scams
